Many Countries Approve The Use Of Voip
In every country there is a quality control department, checking a product to approve, once approval is over, a company can get business from other country. This is not like other marketing style. Multi-level marketing is different user only marketing a product, once user is satisfied, he recommend the same product to someone close. Nevertheless, for this recommendation company pays him five to ten percent commission, however based on recommendations a person can get more percentage for recommending a product.

People are not interested in an old network and its telecommunication products; people are interested in new and latest products. This is the advantage for a company to get popularity with public, in case a company involved in old technology, even it is hard for that company to establish their products within birth country. A public requires novel network, only that makes him to connect with people and enjoy chatting each other and other facilities offered through network services. Same time, there are many usable in previous tech, it is added in modern tech, apart from that new add on facilities are supporting a network in latest technology that is the reason a business not only shines in local country and it reaches to more and more countries. When product like VoIP phone, a highly recommendable and vastly common office phone system singapore is able to get popularity with public, there is no wonder it is reaching entire world, because communication products are highly required now in the world.
Know what agile meetings are
Dexterous gatherings are compelling punchy gatherings that are fundamental for Agile Team’s viability. Light-footed group gatherings should sprint in a similar successful manner day by day. There are a couple of significant focuses to remember, while thinking about a dexterous gathering. Light-footed gatherings ought to consistently be an every day event. Dexterous gatherings start simultaneously consistently. The fact is to bring the entirety of the colleagues in the know regarding the current accessible data and the advancement that has occurred on and inside the undertaking. This is basic for having the option to arrange the group and their work adequately. Gatherings ought to consistently hold a reason that is clear to all gatherings engaged with the group gatherings.
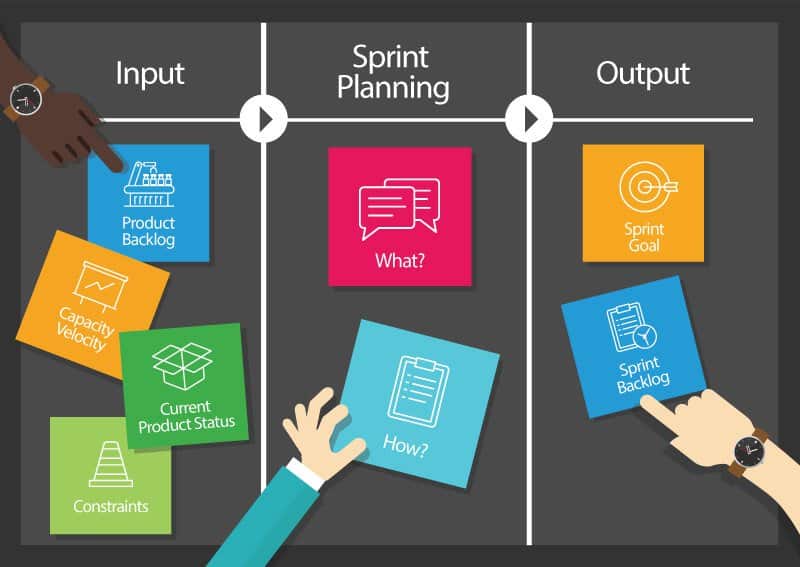
Partners ought to be available in the gatherings in some structure and ought not just be given documentation of the gathering at a later stage. Each gathering ought to have a plan that has been shaped before the day by day meeting and these plans ought to be clung to, so the time period for the gathering is not dismissed. Objectives and targets ought to consistently be talked about ahead of time and not at the hour of the gathering. Each colleague should portray in a nutshell the work that they have done since the earlier day’s gathering. Each colleague should portray in short the work that they intend to accomplish for the next day’s gathering. Each colleague should feature any issues that they are having accomplishing their objectives or notice any checks or obstructions that are impeding their accomplishing their objective. There ought to consistently be a sprint down of deterrents or issues referenced and examined.
The gathering ought to be held with a white board presents for objectives to be recorded and organized. Gatherings ought to be kept to at least around fifteen minutes and a limit of 25 minutes relying upon the size of the group. Group gatherings ought not be indulgent and hauled out. Subjects ought to be kept short. On the off chance that a subject could prompt a conversation, it will be set on a sprint down of things to be examined between the applicable gatherings after the gathering in more prominent profundity and see this Agile Poker. The everyday gatherings ought not just become status reports of each colleague’s advancement. Group gatherings ought to consistently incorporate all gatherings included and be on a vis-à-vis premise if conceivable. Gatherings should hold an incentive for all colleagues. in the event that not, the gatherings become unprofitable endeavors.
Hire best cyber security services
As we all know the need for IT Security Company is highly increasing in current trend. This is because the businesses are in the circumstance to safeguard their information from cyber attacks. In order to get rid of these hassles, the help of cyber security services is to be consulted. As there are more companies which tend to offer different kinds of security services, one needs to be more careful in choosing them. Some of the best considerations for choosing these services are revealed here.
Experience
Before approaching any security consulting company, their experience should be taken into account. Their journey in the field of cyber security should be analyzed. The service which tend to have greater experience and the one that is highly successful in providing the best security system for their clients should be approached.
Technical assistance
The service should be capable of providing the best technical assistance. It is to be noted that the technical issues may occur any time and once there is an issue, it should be fixed immediately without delay. In such case, the service that is capable of offering the top notch technical assistance should be hired.
Advanced security services
Obviously security is the main reason for why these services are being hired. In such case, the service that can offer advanced security system should be taken into account. They must be capable of carrying out the highest level of security processes that can favor their clients with the highest security features.
Read the reviews
In order to know about the specialization of a service and to know about quality of their work, their reviews are to be read. In case, if the reviews sound to be satisfying the best cyber security services in singapore can be hired for experiencing better security system.
Straightforward HostGator vs Bluehost in Online World
Internet Marketing is gearing up and this is the time for web hosting companies to play their match. There are thousands of web hosting companies and each one of them claims their support to be the very best. They attract the net users by offering a variety of services, but would not respond to you when there’s a problem. My first and foremost guidance for the web users would be to read the HostGator review prior to deciding your host firm.
HostGator is not a new organization to the online world. They are in existence and are providing commendable service. An individual cannot pinpoint any criticism on this host. In the HostGator review you may understand that this is the hosting company that is serving the web users for longer duration. They provide 99.99% uptime guarantee, so there is absolutely not any possibility of your server shutting down any moment.
HostGator review also stress on the qualities of their plan. They are the only web hosting skilled company that provides unlimited disc space, unlimited e-mails, unlimited data transfer and so forth. They also provide a 45 days money back guarantee on HostGator vs Bluehost while others offer just 30 days. In the event, if for any reason you do not need to take their support, they do not hesitate to return your money.
Web users who have obtained the support of HostGator have contributed excellent reviews on its customer care. With numerous computer literates in their business, they can address any of the issues your site faces. Issues are immediately solved through e-mail or phone.
HostGator helps the beginners with many offers. To make their website easy and user friendly, HostGator provides free website builder, website templates. These tools can assist the non-programmers to develop their site easily.
HostGator is a frequent award recipient for its excellent service. Some of the awards to highlight here are: Fastest Growing Private Company provided by Magazine, Readers Choice Award provided by About.com best reseller hosting, Editor’s choice award given by Findmyhost.com. Their award journey and support does not stop here. They still continue to acquire more and more loyal clients internationally. The reason for their success is their dedication, dedication and professionalism.
Performance
The functionality from HostGator’s servers is exceptional. Hostgator place much tighter limits on the amount of sites sharing the same server in contrast to many other shared hosting providers. This gives better reliability since less strain is placed on the servers; and it also greatly enhances the rate at which your web pages operate.
Server performance is just another one of the key areas where Hostgator distinguish themselves from the crowd of other web hosts.
Work of Virtual Network Operators in Micro-Multinationals
The Wall St. Journal has defined the term micro-multinational to mean company that from its inception is based on security but maintains a less-costly skilled workforce overseas. According to the Journal, these firms are the darlings of venture investors, not just because of their lower labour costs but also due to the increased productivity caused by 24-hour media and operations. Micro-multinationals base their headquarters and economically leverage key resources across the planet for certain abilities and jobs, such as development in India and production in China.![]()
A key driver in making them effective and efficient is the selection of the communication system used to seamlessly connect their respective locations together. Thus one of the first items in their to-do lists would be to design and implement an effective and secure network that could do everything from sharing information and sending mails to leveraging the network for VoIP calls or video conferencing.
These correspond to additional features in the deal that may or may not need. As such, it is important to ask. By way of example, you may want your choice for best VPN supplier to permit P2P usage. You wouldn’t need to end up in a situation where you are protected from malicious internet attacks but you cannot do the things which you would like to do online because your VPN service is blocking the sites which you want to go to. Assessing the community, from state coverage to access options, safety integration, and pricing could result in quite a lengthy selection and implementation procedure.
To help facilitate and expedite this procedure, a Virtual Network Operator VNO provides end-to-end controlled solutions, working with community providers around the world offering best-of-breed last-mile infrastructure and implementing end-to-end Quos consistency. These vpn reddit can evaluate and plan for a complete, secure, and flexible network solution that is ready to grow with the requirements of micro-multinationals. By working closely with these organizations from a worldwide network implementation standpoint, a VNO is ideally positioned to help guide them through the maze of network functionality, accessibility, redundancy, and layout choices.
Safety and reliability of the network infrastructure are also Important variables for micro-multinationals. Since these organizations have departments scattered around the planet, they will need to have a WAN that functions very similarly to a LAN, with secure network services like community VPNs or MPLS solutions augmented by firewalls and Intrusion Prevention Services IPS. Furthermore, companies will probably need to safely incorporate some employees who need to access this network from remote locations as they travel or work at home. As organizations grow, they may leverage more real time information applications, video conferencing, and VoIP solutions to decrease costs. These services need the exact secure network infrastructure with the capability to grow to meet demand and expand to include new kinds of services.
Fix Problems Associated With DLL Files
The best approach to take care of DLL issues are dictated by the wellspring of the issue. The wellspring of DLL errors can be separated into two classes. There are errors related with application, and afterward there are errors due to malware.
DLL Download Errors Due to Malware
The most widely recognized reason for DLL errors is malware. The best line of assault against malware is a decent offense. Antivirus and hostile to spyware security introduced on your PC is useful, and doubly so when it is running sweeps of your framework consistently.
Other great tips incorporate avoiding opening messages from obscure beneficiaries and continually checking the legitimacy of a file prior to downloading it from the web. Be that as it may, even the most proficient PC designs in some cases experience difficulty with malware influencing their frameworks.
It is practically outlandish not to, taking into account that there is presently more malware being created at some random time at that point genuine programming.
DLL Errors Associated with Application
Most of the unityplayer.dll not found errors brought about by an application can be wiped out by reestablishing the first DLL file. To do this, you will initially have to check for updates or fixes distributed by the producer of the application being referred to. In the event that none can be discovered, you can look for the particular DLL file on the web, at that point download and reestablish it.
What is a DLL Library?
What is normally alluded to as the DLL Library is really the file extension.dll which represents dynamic link library. DLL files are gatherings of little projects usually utilized by more than one program.
The formation of DLLs has permitted software engineers to use pieces constantly of what is as of now on your PC to run their fresher projects. This implies that the more up to date programs occupy less room.
Probably the most ideal approaches to dispose of DLL errors is to utilize a believed library cleaning programming. Adulterated and undesirable files can stop up the vault and hinder your machine’s exhibition.
It is critical to keep your vault running fit as a fiddle by utilizing programming that gets results. Become familiar with how library cleaners do not simply kill DLL errors, however they can likewise deal with other run time errors that plague any PC.
Tactics on How to Choose the Right VPS Hosting Plan
Prior to pursuing a VPS facilitating plan, it is imperative to initially comprehend what is the issue here. VPS which is short for virtual private workers, is a unique programming used to parcel a solitary machine with the goal that it capacities as numerous PCs. Generally, numerous destinations are facilitated on a solitary PC. VPS is a truly helpful arrangement since customers do not have to put resources into a solitary committed machine to appreciate the advantages of having devoted assets. The expense of the worker will at present be divided between a few customers, however the expense per customer is altogether lower. Customers will appreciate the advantages of having a devoted facilitating account at much lower expenses. For example, they have more command over their workers and they do not need to stress over their own locales being influenced by different sites. Site execution is additionally more steady and dependable as worker assets are devoted to each VPS account.
So how to approach picking the privilege VPS plan?
Tip 1: Choose the correct OS. Your VPS plan can be fueled by one or the other Windows or Linux. Each has its own upsides and downsides. Everything relies upon how agreeable you are with the OS. In the event that you have the assets to deal with a Linux worker, at that point definitely, feel free to pursue a Linux VPS plan. Be that as it may, on the off chance that your current site has been created utilizing Microsoft’s foundation, at that point you have next to no decision except for to go with the Windows VPS workers.
Tip 2: Sign up for an arrangement with the perfect measure of assets. Remember that VPS plans are downsized forms of a devoted worker. So on the off chance that you can bear the cost of it; attempt to go for an all the more impressive arrangement. A better quality Windows VPS plan is typically less ground-breaking when contrasted with a devoted worker facilitating plan, however the assets allotted should sufficiently be to take into account your necessities. Smash and hard circle space should be at the first spot on your list. More RAM for the most part implies more dependable execution. You will find that there are 2 sorts of RAM accessible ensured RAM and burstable RAM. Ensured RAM is the thing that is designated to you.
Tip 3: Finally, make certain to join with a legitimate facilitating organization. What you see on a facilitating site may not be precise on the grounds that anybody needs to advance their own administrations. In the event that you do a tad of examination, you will before long have the option to decide the more respectable VPS facilitating organizations.
Prologue to Artificial Intelligence
Presentation
This arrangement of articles is centered for the most part on the subject of Artificial Intelligence AI. We will begin by taking a gander at what AI is, and spread the different manners by which it very well may be executed and applied utilizing PCs and present day innovation in additional articles.
Section 1 – An Introduction
Man-made reasoning is an exceptionally wide field, and a long way from being segregated to processing it envelops numerous different trains, for example, theory, neuroscience and brain research. It is imperative to note however, that as opposed to simply looking to get insight, AI experts look for additionally to construct or make it. The utilizations and uses of AI are numerous and fluctuated, and albeit many consider humanoid robots when we examine AI, you might be amazed to realize that we as of now experience applied AI in our everyday lives.
Computer based intelligence is brimming with central issues – how does a substance either natural or mechanical think? How can it comprehend or tackle an issue? Could a artificial intelligence Colombia be keen? What is knowledge? The response to these inquiries may not be simple, however there is an answer gazing us in the mirror so we realize the mission to discover is attainable.

Through this arrangement of articles I will investigate the a wide range of approaches, sub-fields, applications and questions that we experience while investigating this immense and energizing field of exploration.
Section 2 – What is AI?
Right off the bat I might want to state that the term Artificial Intelligence AI implies various things to various individuals. Indeed even the words we use to portray the point are vague. The term counterfeit can have quietly extraordinary importance; consider what we mean when we allude to ‘fake light’. This is genuine light that has been made by a man-made source. It works precisely as we would anticipate that light should work, and from a physicists perspective it essentially ‘is’ light. At the point when we allude to ‘fake grass’ in any case, we utilize the word fake to mean something unobtrusively unique. Fake grass is not grass. It’s anything but a plant, it is not made of a similar material as the plant, and it does not share all the properties of genuine grass. It does anyway play out the principle elements of grass sufficiently, and may frequently trick individuals into accepting that grass is available.
The term knowledge is likewise not entirely clear, thus we end up with some totally different meanings of what AI really is. The definitions we think of anyway will in general fall into a one of two classifications – they are either centered around the cycle used to accomplish the objective, or on conduct. For instance, Luger and Stubblefield characterize AI as ‘The part of software engineering that is worried about the computerization of savvy conduct’ Whereas Winston characterizes it as ‘the investigation of the calculations that make it conceivable to see reason and act’.
We likewise should consider how we measure achievement, and again there are several normal guidelines. We will in general either evaluate our framework when contrasted with human execution, or against an ideal idea of insight regularly alluded to in the field as ‘soundness’. A framework is sane on the off chance that it settles on the right choices.
Surefire Tips to Protect Your Computers from Hackers
Hacking assaults are steady concern and perpetual migraine for any organization chairman. All the more strikingly and incidentally, the best protection against them originates from hackers themselves. Yet, these hackers are of an alternate kind and breed – they are ‘moral hackers’. While organizations and government associations the whole way across the world are spending gigantic aggregates on employing proficient organization security specialists or moral PC hackers, you can make your PC secure by being somewhat more cautious and by keeping your framework furnished with cutting edge hostile to hacking arrangements. How about we perceive how
- Continuously utilize the most recent form of hostile to infection programming applications. With great enemy of infection programming, at whatever point a hacker attempts to get to your machine you would be cautioned about it so you can make essential strides before any harm is finished.
- Continuously keep the firewalls in dynamic mode as it will forestall unapproved section by the hackers.
- Continue checking the projects running on your framework consistently. In the event that, you run over some program that you probably would not have introduced or which does not shape part of standard working framework, at that point be ready and cross check it as it may be a type of spam.
- To limit hazard against infection assaults and hackers, stay up with the latest as it permits the machine to know about the most recent found security gaps. In the event that you do not do that, you are simply giving open greeting to the hackers who simply advance from each fizzled or dealt with’ hacking assault.
- Never overlook the patches when they show up for establishment. Typically what happens is that a hacker makes an approach to enter your PC through some normal projects. By introducing security fixes and fixes you make your PC safe from hackers as they are created with the sole thought process to fix security related issues how to hire a hacker safely.
Indeed, these tips are only the essential precautionary measures to protect your framework from the hands of hackers. In any case, it is smarter to take help of specialists to deal with safety efforts. Numerous organizations these days utilize moral hackers with information on network security, splitting and hacking to counter the hazard of criminal hacking. Moral hacking is subsequently quick turning into a picked profession choice for youthful IT geniuses given the way that the IT security market overall is developing significantly. There are different courses accessible for PC hacking and network security preparing. Proficient splitting instructional exercises and different courses set it up security experts for appealing professions in large associations.
What is all about media storage solutions?
The accessories and furniture Storage have progressed through the years. Entertainment facilities, and cabinets, CD racks are created for this need. Made from the CDs to keep everything up to your 52 inch LCD HDTV, there is not any shortage of size and design options. Computers screens and A TVs have diminished in size to take up the proliferation of mix of products, space to home the press and them they need has exploded.
Every Media storage alternative has its own unique features and design styles: There are a number of kinds of cabinet setups and racks which can enable you to save space. Among my favorite is called a Spinner. It is comparable to a tower, but has sides which you twist the rack, or could turn. There are loads of other choices, such as constructed in stand-alone wood or metal racks, racks, and entertainment centre systems. You can save plenty of space with a TV wall mount by removing the TV for your media needs.

Cabinets, shelving and while like tacks, have the benefit of concealing your media. The doors on a cupboard of entertainment system are a terrific addition to your home decor, in addition to adding privacy. When deciding on remember to include the protection factor. While there are lots of styles and designs to select from, you should be certain that you keep the cases for protection, and that your CDs and DVDs are stored. Additionally, there are harm preventing storage features that protect your media from the components you will evaluate and other cases. Check to find out if these data media safes attributes fit your media needs. Then a cabinet or entertainment center with doors might help protect from dust, hair, and travel nuisances and without special accessories if protecting your media is a storage priority.
Even Other and flash media cards and discs need your attention. Do not leave the media since they are the most likely to loss and damage, the reasons for locating a media storage solution. Just As with a media storage cabinet any household storage products and electronic media storage components can be created from a vast array of levels and substances of craftsmanship. As this will save you unnecessary and hassle costs later on, always pick the quality product that you can afford.
